BLACK SATURDAY EMAIL – Sensitive information from over 73 million AT&T customers might be available on the dark web
On Saturday, while over 80% of Americans were preparing for their Easter celebration of light, almost eight million people received an unwelcome email from AT&T that their personal information may be on the dark web.
AT&T has initiated an in-depth investigation into a significant data breach that resulted in the personal information of millions of its customers being leaked on the anonymous darknet. This cybersecurity incident has potentially compromised the data of approximately 7.6 million current and 65.4 million former customers.
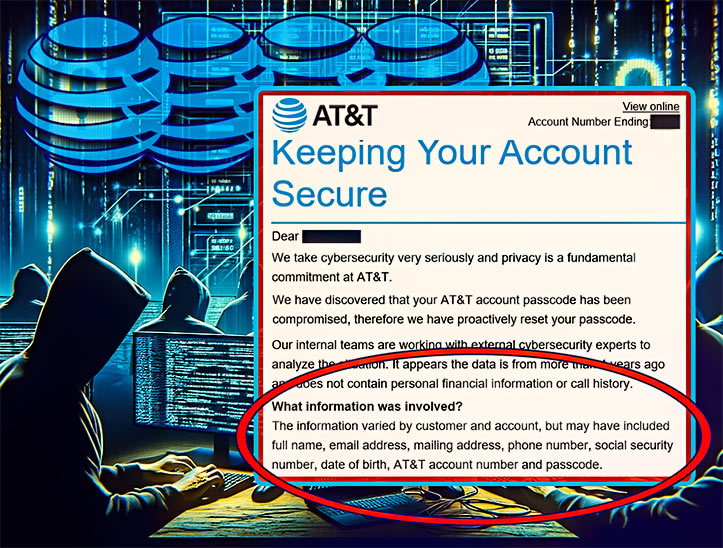
The leak involves sensitive personal information, including Social Security numbers, full names, email and mailing addresses, phone numbers, dates of birth, AT&T account numbers, and passwords.
AT&T will be investigating its vendors
The company has indicated that this data appears to originate from 2019 or earlier and has been rigorously investigating the source of the leak, whether it be from AT&T’s systems or one of its vendors. So far, AT&T has found no evidence of unauthorized access to its systems that could have led to the exfiltration of this data set.
AT&T does not publicly disclose which vendors can access its customer information for security and privacy reasons. However, it’s common for large telecommunications companies to partner with various third-party vendors and contractors for services such as customer support, billing, equipment provisioning, and network maintenance.
These partners may have access to customer information as necessary to fulfill their contractual obligations.
AT&T has taken several immediate actions to safeguard affected customers in response to this breach. The company has reset the passcodes of the 7.6 million customers currently impacted and is in the process of reaching out to all individuals with compromised sensitive information.
AT&T is offering those affected complimentary identity theft and credit monitoring services through Equifax, Experian, and TransUnion. Furthermore, the company has encouraged all customers to monitor their account activity and credit reports vigilantly.
AT&T has enlisted the help of external cybersecurity experts. Despite the scale of this breach, AT&T has reported that the incident has not had a material impact on its operations.
TechCrunch, the first to report on the reset of passcodes, notified AT&T on Monday about the presence of encrypted passcodes within the leaked data, which could potentially be utilized to access AT&T customers’ accounts.
The publication chose to postpone the release of its report until AT&T had initiated the process of resetting the passcodes for affected customer accounts.
In its coverage, TechCrunch highlighted that this incident marks the first instance of AT&T recognizing that the leaked data is associated with its customers. This acknowledgment comes three years after a hacker claimed to have obtained records of about 73 million AT&T customers.
In 2015, AT&T agreed to pay a $25 million fine to settle an investigation into data breaches at call centers in Mexico, Colombia, and the Philippines. These breaches reportedly allowed employees to steal personal information, including names and complete or partial Social Security numbers, of about 280,000 U.S. customers.
Before that, in 2014, there was an incident involving unauthorized access to AT&T’s customer information, including Social Security numbers and dates of birth. This breach was attributed to an insider—specifically, an employee who inappropriately accessed customer data.
AT&T doesn’t have exclusivity on data breaches
Since 2018, T-Mobile has identified nine breaches. The company reported that data from 37 million accounts was leaked between November 2022 and January 2023.
Although no data was breached, a Wireless Estimator investigation uncovered that T-Mobile notified a vendor to log out of its network and cease operations since the vendor was providing services covertly from Lebanon.
Around August 18, 2021, T-Mobile revealed that more than 76.6 million current and former customers’ information had been accessed.
In a blog post, CEO Mike Sievert said the hacker, later found to be a 21-year-old American who lived in Turkey, “leveraged their knowledge of technical systems, along with specialized tools and capabilities, to gain access to our testing environments and then used brute force attacks and other methods to make their way into other IT servers that included customer data.”
Verizon appears to have had the fewest breaches. In 2016, a data breach involving Verizon’s enterprise customer portal exposed the contact information of 1.5 million business customers. The breach was relatively limited in scope, affecting only basic contact information and not including customer passwords or other sensitive personal information.
In 2017, a misconfigured cloud server managed by a third-party vendor exposed data from as many as 14 million Verizon customers. The exposed data included names, addresses, account details, and PIN codes.
Although Verizon has had more minor breaches, no sensitive customer information has been exposed. However, on February 7, 2023, the carrier notified the Maine Attorney General that the company experienced a data breach resulting in the theft of sensitive information of over 63,000 employees. The breach included Social Security Numbers and other sensitive information on employees.